AJ Piscitelli, PMP
Project Manager | ERP Solutions Provider | Cloud Architect
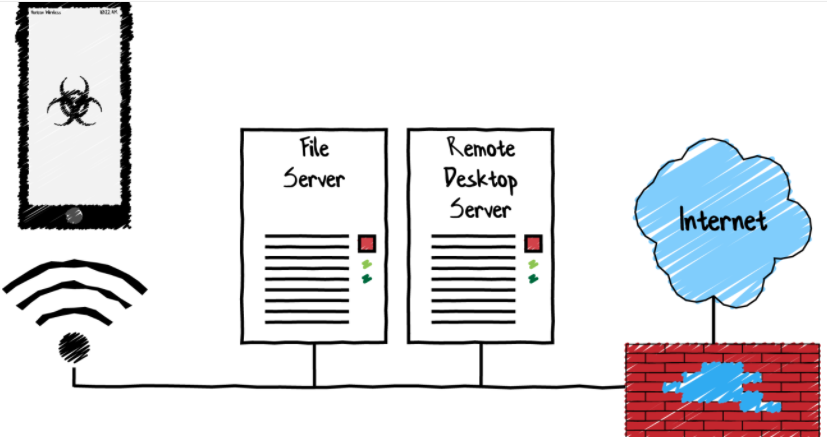
A recent poll that I gave as part of a presentation a few weeks ago showed that nearly all fabricators in our industry are using Wi-Fi at their facility. I can’t remember the last time I visited a facility that didn’t have Wi-Fi available. But are you exposing yourself to attacks by using Wi-Fi at your facility?
Let’s face it, we must have Wi-Fi to run our operations. Employees use tablets on the production floor to look up information about a product, mobile scanners are used to load products onto a truck and adjust inventory, and floor stations may use Wi-Fi instead of running a network cable to that location. It’s part of your infrastructure and part of your operation. Since we must use it, we should secure it as best we can. Let’s go over a few simple tips on how you can secure your Wi-Fi.
Always Require a Password
This is a straightforward and often first step to securing your Wi-Fi. You should not have any unprotected Wi-Fi access within your facility. Unsecure Wi-Fi can provide access to people who you may not want on your network. Remember, Wi-Fi signals penetrate past the walls of your facility. A neighbor or someone driving by after-hours could gain access to your network and cause problems. By placing a password on your Wi-Fi, you help prevent these types of attacks.
Separate Corporate, Employees and Guest Networks
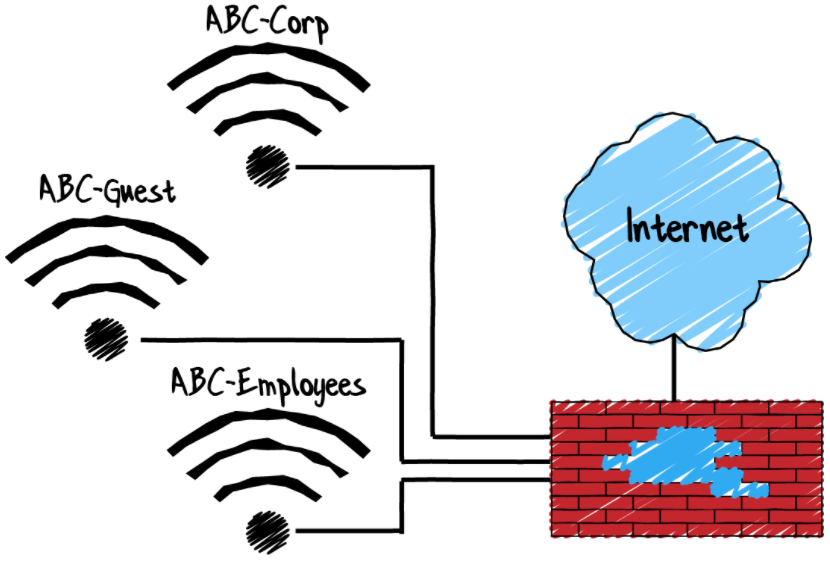
About half of the people I surveyed had only one Wi-Fi network (SSID) for their entire facility. This meant that guests and employees had unfettered access to all the other equipment on the network. Even with eliminating malicious intent, compromised computers and mobile devices can wreak havoc on your network if connected.
The simple solution here is to separate the networks and restrict who has the ability to access each. The Corporate network should only be used for domain-connected devices that need to access the local domain controller and file shares. The Employee network is for employee devices, such as phones and tablets, and may have access to certain corporate web assets for their daily duties. The Guest network should only have access to the internet, and possibly one or two printers.
Most enterprise-grade networking equipment can broadcast at least five different Wi-Fi networks (SSIDs) on the same access point (AP). A lot of the setup behind this is done with VLANs, which I plan to discuss in the next blog entry. You can do this without breaking the bank. There are some relatively inexpensive options on the market, and I’d be happy to discuss them with you.
Protect those passwords

Now that you’ve separated the networks and created passwords for each of them, you must secure those passwords. The Corporate network password should not leave the IT department. As new equipment is set up, the IT department can add the Corporate network password to the computer. The Guest network can be posted publicly, but only in locations where they would be expected to access, like conference rooms.
The Employee network creates some additional possibilities. You could set up RADIUS and authenticate using the employees’ AD credentials, but I would assume that most of your floor staff does not have their own AD account. This means that a simple password may be the best approach. This password should not be posted, but you should anticipate that it will be shared among other employees. Therefore, it is important to limit the access of this network, as discussed above.
Conclusion
Every little bit helps when it comes to security and these are just a few simple steps that you can take to better secure the Wi-Fi within your facility. Let me know what steps you are taking or if you’d like to discuss how to better secure your facility.
