AJ Piscitelli, PMP
Project Manager | ERP Solutions Provider | Cloud Architect

This is the second part of a true story from an IT Vendor dealing with a phishing attack at a small contracting firm, „ABC Contracting.“ If you have not read the first part, you can find it here: Phishing Story Part 1. As with Part One, the names and identities of people and companies in this story have been changed for privacy.
“I’m having some problems”
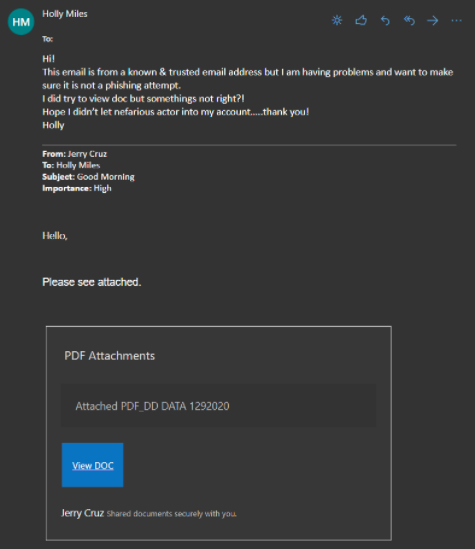
A couple of weeks after the phishing attack, I got an email from a different employee at ABC Contracting, Holly Miles. Holly works in the accounts payable department at ABC. Her email says that she received an email from a trusted individual, but she’s having trouble downloading the document that was attached. I saw the original email that she forwarded in her message, and a combination of frustration and disappointment began to flood in. It was from Jerry Cruz.
Damage Control
Any time these things happen, I immediately go into damage control. I call Holly on her cell phone right away.
Me: „Hi Holly.“
Holly: „Hi!“
Me: „Holly, I’m not going to be upset; I’m not going to be mad at you. I just need to know right away, did you type in your password while attempting to download that document from Jerry?“
Holly: „Yes. Did I mess up?“
Me: „Unfortunately, yeah. Jerry’s account was compromised a few weeks back. They were supposed to take care of it, but it’s apparent that they did not.“
Holly: „What do I have to do?“
Me: „I’m going to reset your password here in a minute. If you’ve used that password anywhere else, you’ll need to change those too. Make sure that any new passwords you create are very different than the compromised one. These guys are smart. They’ll try different combinations of numbers and letters.“
Holly: [Sighing] „Okay.“
Luckily, Holly’s account had Multi-Factor Authentication, or MFA, enabled. This means that, even with her password, they could not easily access her account. While I knew that they couldn’t get in right away, I still changed her password quickly. I also sent an email to everyone in the company about Jerry Cruz and gave them another reminder about being careful when opening links in emails.
The next step was a bit harsh but necessary given the circumstances. I blocked all emails from Jerry Cruz into our Exchange. I knew that this could mess up future business between ABC Contracting and XYZ Surety, but the risk was too great. I let ABC’s president know that any future emails from Jerry would be blocked. Luckily, everyone at ABC trusts my judgment, and there was no pushback.
A Strongly Worded Email
As I wrapped up damage control, I then focused on XYZ Surety. After being blown off during my last call to them, I was frustrated and frankly angry at their lack of urgency in addressing this issue. I asked the president at ABC if he knew anyone else at XYZ Surety. He stated that he knew XYZ’s president, Robert Thompson, but didn’t have his email.
Luckily, most organizations use the same email naming conventions for all their users. So, all I had to do was follow the convention on Jerry Cruz’s email to get Robert Thompson’s email address. By the way, the attackers know this trick too.
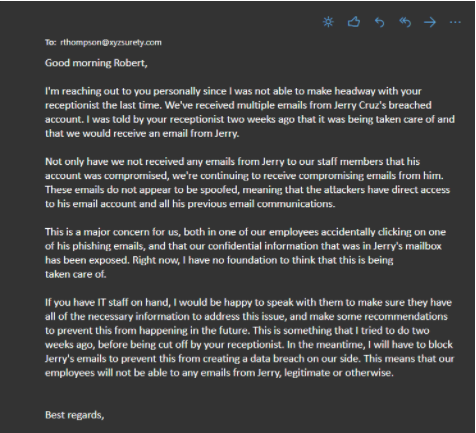
The letter I sent was blunt, to say the least. I told Robert that this has been an issue for at least two weeks. I was cut off by their receptionist the last time I tried to contact them about the issue. I have grave concerns about our (ABC Contracting’s) confidential information being exposed and have zero confidence that they have or will take care of this problem. I also notified Robert that I would be blocking all emails from Jerry Cruz, legitimate or otherwise, to protect ourselves from a similar data breach.
Robert replied with an apology and his cell phone number. Finally, some progress! I called Robert right away. I wanted to get him on the phone while this issue was fresh in his mind. We discussed what had happened, the ramifications, and what to do with Jerry. It turns out that Jerry knew that his account was compromised, said he was going to take care of it, and did nothing. Robert was close to firing him over this incident. That is how critical IT security is today; you could possibly lose your job over it.
I suggested to Robert that he talk with his IT vendor about Multi-Factor Authentication (MFA). Robert had no idea what MFA was and asked me to send him some information so he could bring it to his IT vendor. Again, I was shocked that a company dealing with financials wouldn’t have it enabled for all of their employees. I also provided Robert with some additional recommendations to increase his security. He agreed to keep me updated on Jerry’s account so that I could unblock him.
I started to feel a little bit better. Overall, it could have been worse. MFA saved ABC Contracting and will hopefully help XYZ Surety as well.
I hope this story was both entertaining and educational. As you have read on how important it is, I plan on discussing Multi-Factor Authentication in the future. Make sure you subscribe, so you don’t miss out! As always, if you’ve enjoyed this story, leave a like and a comment. If there are other areas that you’d like to see, let me know in the comments. It helps me to determine what to cover in the future.
