AJ Piscitelli, PMP
Project Manager | ERP Solutions Provider | Cloud Architect

As we head towards the end of National Cybersecurity Awareness Month, I thought I’d discuss what I consider one of the most dangerous cyber threats today: Phishing. Phishing is when attackers try to steal personal information from you by pretending to be someone else, fake surveys, or other forms of social engineering. It is the most successful strategy that attackers use to gain access to your network. Attackers are getting more and more sneaky and creating more ingenious traps to capture your credentials and personal information.
We hear about phishing all the time, but what is not often discussed is a real example of an attack. Fortunately, I connect and talk with many IT experts, and I often hear about their actual experiences with attacks. I think it is important to share these with others to help spread the knowledge around. If you would like to discuss some of your stories, please let me know!
This story will discuss one case of phishing (with names changed, of course), the impact that occurred, as well as the mitigation steps taken after the fact. This story is from an IT vendor at a small contracting firm called „ABC Contractors.“ This is what I would consider a very mild attack. While it is not the most exciting of stories, it is a true story and does a good job of highlighting how easily an attack can occur.
Lastly, if actual examples like this are of interest to you, please like and let me know in the comments below. It helps me determine what content is of interest to you.
„Is this legit?“
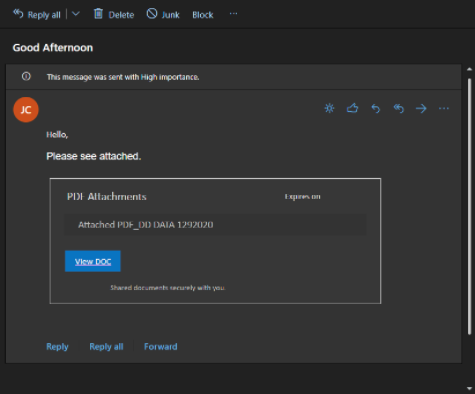
In the morning, I received an email from the president of one of my clients. “Is this legit?” It’s not unusual for me to get these emails occasionally. I don’t mind seeing these emails, as I’d rather be safe than sorry. I get so many emails though that sometimes I don’t see them for a few hours. I worry that the damage might already be done. I examined the email forwarded to me. It’s from Jerry Cruz. I look at the link, and it is pointing to a OneNote document. I’m not intimately involved with the inner workings of this customer, so I’m not familiar with Jerry or his company. Before I click on the link, I do some digging.
Investigation
I check the email headers, it passed all of the spam checks, and SPF and DKIM records appear OK (I’ll cover SPF and DKIM in a later blog post, but know that they are part of a system used to combat email spam and spoofing). The address isn’t spoofed or a mistyped domain, either. I look into the domain and the company to make sure they are legitimate. Everything looks OK about the company, but the OneNote link sets off a red flag. I follow up with the president to ask how well he knows the company, and whether they have worked with this person before. He confirms that they have worked with them on numerous occasions, including Jerry, as he is their account rep.
The company in question does bonds for large construction projects. We’ll call them XYZ Surety. Now a lot of these financial companies use third-party products like DocuSign and others to process legal documentation. But it just doesn’t feel right, and I’ve learned to trust my gut over the years.
I load up a secured Linux computer to do some investigation. A secured Linux machine can provide some level of protection over a standard Windows instance, but it’s not 100%. So I take some extra precautions by isolating on the network and sending all of the traffic through a VPN. Paranoid? Yes. But they are indeed out to get us after all!
I know clicking on the link at a minimum may, and often does, let the attackers know that the email address is real. However, if what I suspect is true, they already know it’s real. I click on the link inside my secured environment to see what is waiting for me.
The browser loads up a OneNote document with yet another link inside. This one is a link claiming to be a DocuSign page. Looking at the link, it points to something within Google Cloud’s offering. Let me emphasize this, not Google, Google Cloud. Anybody can run anything on Google Cloud (at least for a while before they catch you violating their Terms of Service). I’m sure at this point it’s an attack. They put in a lot of work to avoid detection. I send an email back to the president at ABC: “Don’t click on it. Scam.”
Now I could have stopped there, but I wanted to find out what they were after. I loaded up a website that previews other websites for safety. Again, I know this lets the attackers know that the email is held by a living, breathing human, but I also know they already know that. My request yields an image of what would have been presented to me: a fake Microsoft Office login page. This page was created to capture username and password combinations. This was phishing. I report the Google Apps server to Google for scamming for them to address.
Looking back at the OneNote, I see that it does indeed belong to XYZ’s Jerry Cruz. This is particularly alarming, as it confirms the worst-case scenario: The attackers have full access to Jerry Cruz’s Microsoft account. They can see all emails, including past emails, any OneDrive documents, any SharePoint documents, etc. What is particularly concerning is that XYZ deals a lot with financials, project plans, and other highly confidential information. ABC’s confidential information is now exposed by XYZ, all because Jerry Cruz’s account was compromised.
Remediation
As an IT consultant, I like to call the company and discuss the attack with their IT personnel. I feel that we should strive to make each other safe and help where possible, even if it is a competitor. In the end, we are all just trying to keep our users safe.
I called XYZ Surety’s main number and reached the receptionist, Sally.
Me: „Hello, I’m the IT guy for ABC Contracting, one of your customers. Can I speak with someone in your IT department?“
Sally: „What is this regarding?“
Me: „One of your employees has had a breach, and I’d …“
Sally: „We already know about it.“
Me: „OK. Umm, I still like to discuss with them the details of the attack so that …“
Sally: „They are handling it.“
Me: „OK … Thanks …“
It is not the response that I like to see, but at least I know that they are aware of it. I let the President of ABC know the details and the impacts of what was exposed and leave it up to him how he wants to address this with XYZ Surety. I feel like I have done good work today. In the end, my users are protected, Google will address the phishing site, and the person who was attacked is already in remediation within his company.
Or so I thought …
I hope you liked the first part of this story. Make sure you subscribe to my posts, as I’ll release the conclusion of this story, including how to protect yourself against these attacks, next week. Again, if you like these types of stories, let me know in the comments below.
