AJ Piscitelli, PMP
Project Manager | ERP Solutions Provider | Cloud Architect
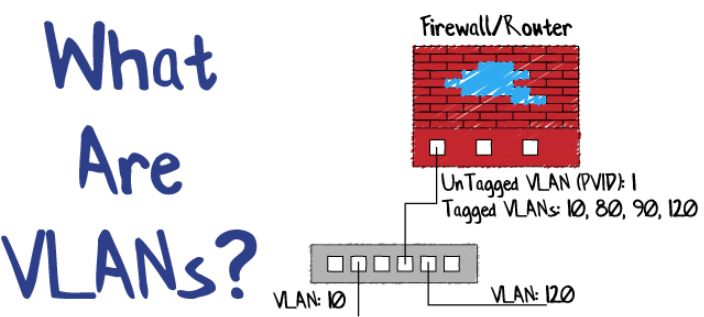
With so many active threats today, it is important today to protect your most important resources. By segregating your network, you can lower the attack surface area of your equipment. We discussed this a bit in my last blog entry about separating your Wi-Fi networks. But do you segregate your network while still allowing some traffic?
How it used to be done
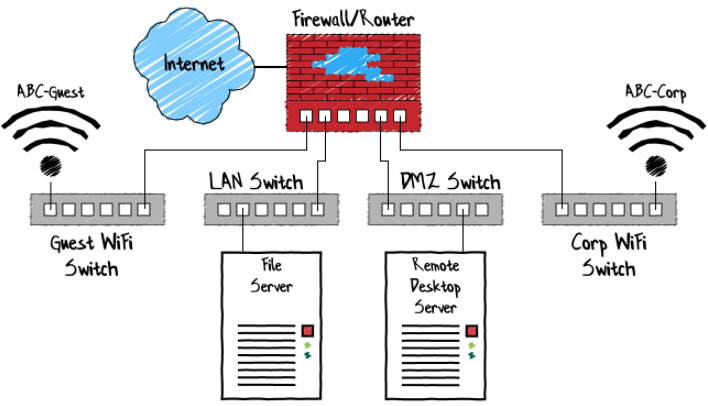
To understand this process, we will look at how networks used to be segregated in the past. Before VLANs, networks were separated physically. This meant that separate ethernet hubs and/or switches were used for each network. Each network would have its own subnet or range of IP addresses for the devices on that network. Traffic would be routed between subnets by the user of a “router.“ Most routers contain firewall components, allowing the ability to allow or block specific traffic between subnets.
By only allowing the traffic between subnets that was necessary, attackers and/or viruses have a harder time spreading between subnets. This isolation in turn protects key network resources. However, the downside of this methodology is much more equipment, wiring, power, and management is needed. This means that segregating networks were often only done by those companies with large pockets.
Enter 802.1Q and VLANs
Way back in 1998, IEEE introduced 802.1Q – Standard for Local and Metropolitan Area Networks (https://ieeexplore.ieee.org/document/753056). This brought us the ability to put an identifying “tag” on a transmitted packet of data that can be used to identify which Virtual LAN (or VLAN) the packet belongs to. This meant that intelligent network switches could segregate traffic by way of this VLAN tag.
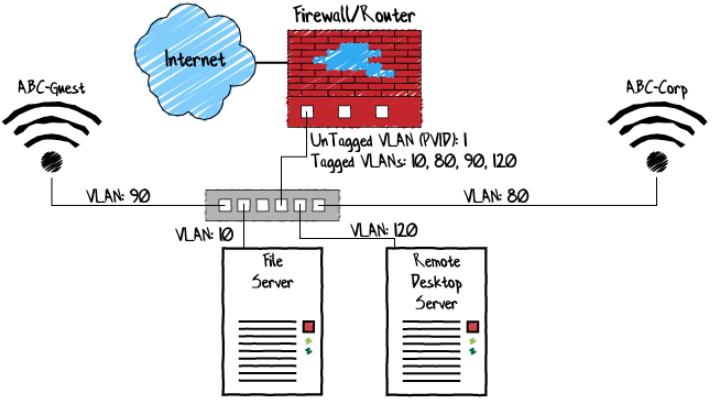
But that was back in 1998. Why do VLANs seem like a new thing?
Well first, it takes time for equipment manufacturers to integrate new standards into their equipment. Additionally, it only applies to newly produced equipment, and most companies don’t overhaul their network too often. But the major reason why VLANs seem new is because the hardware that supports them is starting to come into most companies’ price range.
For a switch to support VLANs, it must be a managed (or “smart” in some cases) switch. Managed switches were traditionally very costly in comparison to an unmanaged switch. However, advancements in circuit technology over the years have made the production of managed switches cheaper. So, companies may be more likely to buy a managed switch now, as they are not significantly more expensive than an unmanaged switch.
Getting Started
The first step is identifying the types of switches and routing appliances you have on your network. If you have mostly unmanaged switches and a consumer/retail grade firewall/router, then plan on investing in new networking equipment. If you would like to discuss some of the different options on the market today, drop a comment below or send me a message. I’d be happy to go over what I’ve used in the past and discuss some of the advantages and disadvantages of each.
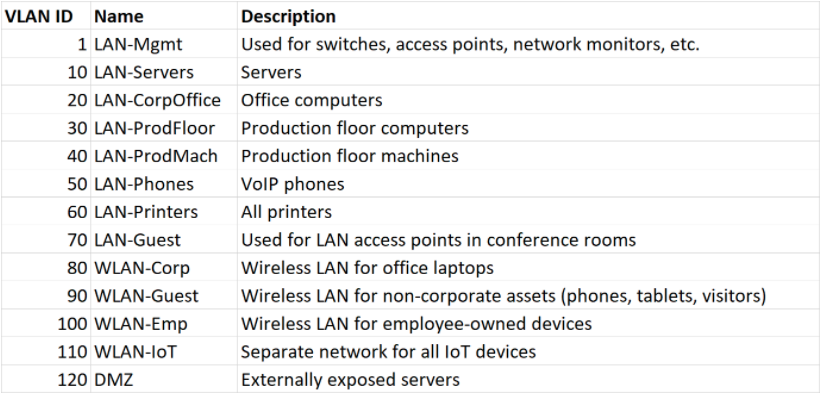
The next step is planning how to segregate your network into VLANs. Come up with a table of VLANs that you would like to use, along with an ID number and description. Keep VLAN ID 1 for managing switches, access points, etc. It will save you a bunch of headaches in the future. An example of a VLAN table is below.
The next part is the hard part. You’ll need to configure your switches, routers/firewalls, DHCP servers, etc., with these VLANs. Every device is different enough that I can’t detail how to configure each one individually.
If this is where you’re not quite sure or confident in going forward, STOP. Making these changes can make your network inaccessible and may force you to have to reset and start all over. Not a pleasant experience. Look for additional resources to help. There are plenty of experienced professionals who would be happy to help guide you through this process. Just be sure to find one who will show you the process so that you can maintain it going forward.
Conclusion
VLANs offer you a way to segregate your network without having to buy separate equipment for each. By segregating your networks and firewalling traffic between them, you can slow down or even stop attacks. But VLANs do require a certain class of equipment and good networking knowledge to set up. I encourage all of you to begin to investigate using VLANs at your facility.
I’ve skipped a lot in this post to keep things simple. But there’s still a ton of stuff I’d love to discuss in this blog post, including packet priority, quality of service, firewall configurations, IP subnetting, DHCP, and layer 3 routing. If any of those topics sound interesting to you, and you’d like to hear more about them, drop a comment below and I’ll add it to my list to discuss.
