AJ Piscitelli, PMP
Project Manager | ERP Solutions Provider | Cloud Architect

What does that mean to you?
In today’s age, breaking into someone’s infrastructure comes with low risk and high reward. Whether it’s from foreign, government-sponsored actors, or from someone who just wanted a challenge, our networks are constantly under attack. I manage several publicly facing servers, and I can see the constant bombardment of people from all over the world trying to break into the networks that I manage.
But what happens when they get in? You’ve seen the news with large-scale data breaches like Equifax, Anthem, and Target where our personal data is leaked to the internet. News reports, dropping stock prices, losing customers, and lawsuits come shortly after. While you or I may not store the same magnitude of data that these organizations have, we also don’t have the same resources to deal with the repercussions of the breach. The data that you store is important and confidential, and Data Privacy Day serves to remind us. When considering what Data Privacy Day means to you, I’d like you to ask yourself three questions:
- What sensitive data is on your network?
- What are the access points to your network?
- How are you securing your data?
Going through each of the above questions should help identify gaps in your network. Only after identifying the security issues on your network, you can better secure yourself from data breaches.

I’ve discussed with many customers about network security over the years, and often one of the first reactions I receive is “I don’t have anything sensitive on my network”. This is of course never true. There is always sensitive data stored somewhere on your network. Let’s look at some examples of sensitive data that you probably have on your network.
Customer Lists and Pricing
While you most likely provide your customers with their prices, you probably don’t want Customer A to see the lower prices given to Customer B. Similarly, you most likely wouldn’t want your customer lists and pricing to be given/sold to your competitors.
Company Bank Accounts / Credit Card Information
Cash flow is the circulation that powers a company to do business. Having all your credit cards compromised or tying up a business bank account in a fraud investigation can cripple business activities.
Employees’ Personal Information
In order to employ staff at your company, you need certain information about the employee on hand such as:
- Full Names
- Home Addresses
- Phone Numbers
- Social Security Numbers (or Social Insurance Numbers for my Canadian neighbors to the north)
- Bank Account Information (typically used with automatic paycheck deposits)
There is an expectation of data privacy between the employee and employer. If you as the employer expose personal employee information, you could be liable for damages associated with the data breach.
Passwords
There are online services that you use often as part of your business. Some of these services include
- Utilities, such as gas, electric, water, phones and internet
- Internet services, such as domain registrars, email providers and web hosts
- Online Banking
- Accounting Systems
- Payroll Services
If these passwords are stolen, malicious actors could gain access to services that are critical to running your business. In addition, these services could be used to further infect and compromise others with whom you do business. It’s not only embarrassing but potentially damaging to the relationship between you and your customers if you are part of the reason behind someone gaining access to their network.
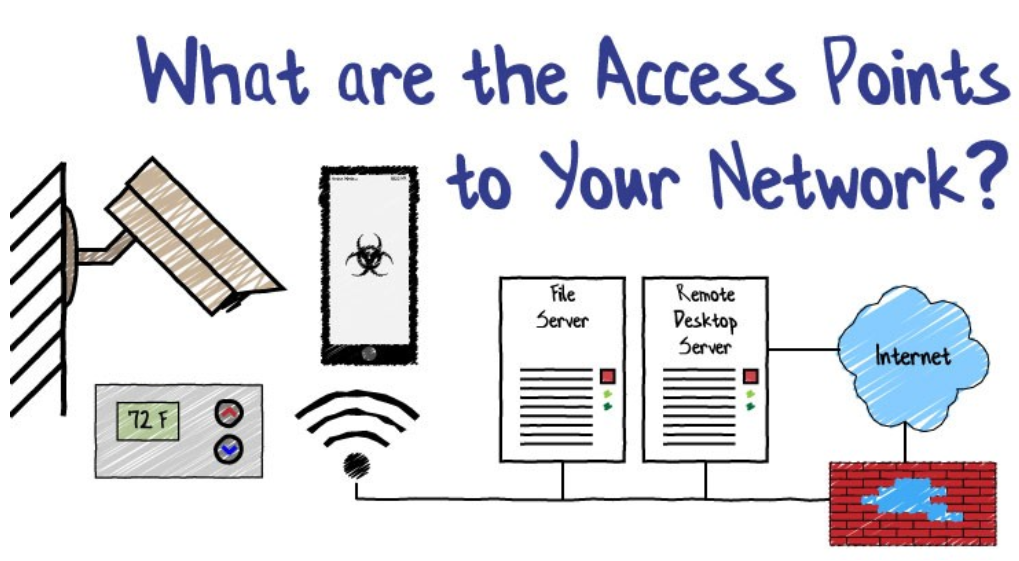
By now, you should recognize that you have sensitive data on your network and some of the potential ramifications of this data being exposed. In order better prevent data from being accessed by those with malicious intent, it’s important to identify the various entry points to your network. Once entry points have been identified, then steps can be taken to secure your network. Let’s look at some of the most common entry points on your network.
Remote Desktop Services (RDS / RDP)
Almost every network compromise that I’ve seen has used a remote desktop server as its entry point. Remote desktop servers provide easy entry to your network and don’t have much in the way of protection. Weak and/or compromised passwords, combined with a lack of brute-force protection, give fast access to your network. Exposing one of these servers directly to the internet without any additional protection is a recipe for disaster. Remote desktop servers should not be directly accessible from the internet. Using a VPN will add an extra layer of security between the internet and the server. If this isn’t possible, steps should be taken to harden the server from brute-force attacks. This includes
- Changing the username for the built-in adinistrator user account on the server
- Setting lock-out limits and duration for any user account that can access the remote desktop server
- Using a third-party program such as RDPGuard that will block an IP address if it attempts to connect to the server too many times with the wrong password
Public Facing Servers Not in a DMZ
In addition to the remote desktop server listed above, any server or device that has ports exposed to the internet, such as a web or email server, should be located within a demilitarized zone (DMZ) within your network. Traffic between the DMZ and the rest of your network should be filtered by a firewall, opening only the ports necessary for the services running on the DMZ servers.
Vulnerable IoT Devices
Today, we use a ton of various devices that have internet connectivity to help run our business. These include things like surveillance cameras, thermostats, and Wi-Fi-enabled plugs & bulbs. A lot of these devices are easily broken into and can expose your entire network. Point-to-Point Tunneling Protocol (PPTP) enabled devices are especially dangerous because they can allow malicious actors onto your network without having internet ports forwarded to the device. Most surveillance cameras come with PPTP enabled, in order to make it easier to connect to the camera via an app. Disabling PPTP will help secure your network, but it’s not the last step. IoT devices should be isolated onto their own network, similar to a DMZ, where they cannot access the rest of your business infrastructure. Additionally, each device should be evaluated to determine if it needs internet access. For example, surveillance cameras that recorded the footage locally, probably do not need internet access. In these instances, the devices should be blocked from accessing the internet.
Open Wi-Fi
I’d be hard-pressed to walk into a factory today that does not have a Wi-Fi setup. Wi-Fi technology has come a long way over the years and has become a stable way of connecting floor computers and systems to the internal network.
I’d also be hard-pressed to walk into a factory where the Wi-Fi isn’t secured with a password. So then why talk about “Open Wi-Fi”? Well, in most factories I visit, there is only one Wi-Fi SSID, and everyone knows the password. If everyone in the factory, including floor workers, knows the Wi-Fi password, is it significantly more secure than open Wi-Fi? How can you secure your servers and critical equipment from everyone’s phones and tablets?
In your Wi-Fi deployment, you should have at least two separate SSIDs broadcasting:
- A corporate SSID that has connectivity to your LAN
- A guest one that only has access to the internet, with no connectivity to your LAN
Only those company-controlled assets, such as machinery and computers that you manage would go on the corporate SSID. Everyone else would use the guest SSID. Use a different password for both, and only give out the guest password.
Open Physical Ports (Ethernet and USB)
It’s very satisfying to set up and manage a facility that has Ethernet available everywhere. Anytime a new piece of equipment or computer needs installing, you can easily plug it in and start working. However, this presents a security risk. Having open Ethernet ports in easily accessible areas can be compromised. Whether it’s someone inside your building who intends you harm, or simply a traveling salesperson whose laptop is full of viruses, they should not be able to easily plug into your network. Most managed switches allow you to disable ports inside the interface. Ports in conference rooms should be limited to internet access only, similar to the guest Wi-Fi.
Just like open Ethernet ports, open USB ports are also vulnerable. Someone charging an infected smartphone by plugging it into an open port on one of your computers could cause problems. Disable the use of those ports via Group Policy, and/or by physically blocking or disconnecting them. Similar to the suggestion with the guest Wi-Fi, you should give people an alternative to prevent them from circumventing your protection. Buy some inexpensive USB chargers that your employees can use and prevent headaches down the road.
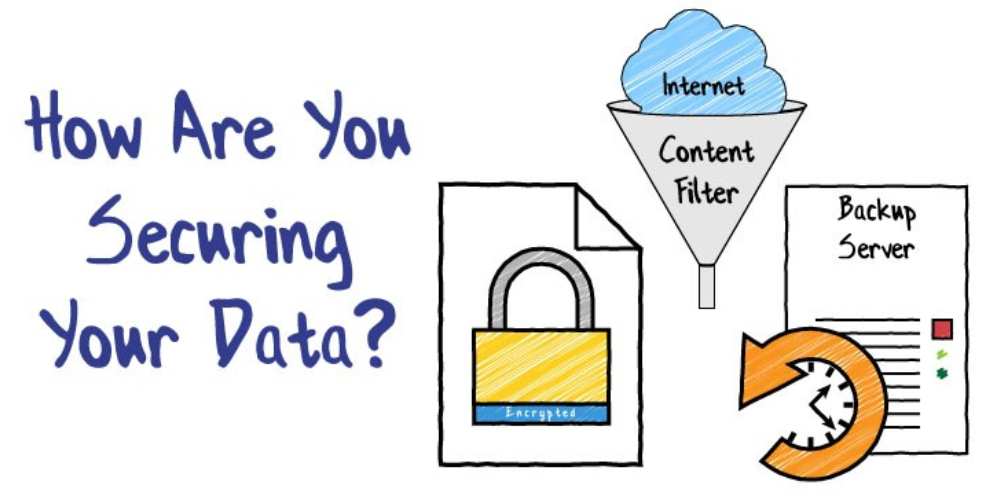
We’ve discussed the sensitive data you store, and we’ve gone over entry points onto your network that can expose that data. The next logical question is, how are you securing your data? A great place to start is closing the entry points identified above. But securing your data means much more than just controlling network access. There are other threats to your sensitive data beyond just network infiltration.
Backups
While backups don’t prevent sensitive data from being exposed, they do help you get up and running after something has gone wrong. I’m not going to go into much detail with backups. I believe the topic is so critical and large that it deserves its own blog post. However, I will say that you need to have backups of everything that is critical, those backups need to be secure/isolated from the rest of your network, and you need to make sure you can successfully restore from those backups. All the horror stories I’ve come across failed in one or more of those areas.
Encryption
Encryption is the process of scrambling data with a key. The only way to retrieve or decrypt that data is to have that key. Sometimes a key is as simple as a pin or password that you remember, or it can be as complex as a hardware token.
Encrypting sensitive data is a large step forward to protecting yourself from attacks. If the encrypted data is taken and the attackers don’t have the key, it is significantly more difficult to gain access to the unencrypted information. If it’s too difficult to decrypt, then your sensitive data may never truly be compromised.
Any sensitive data that can be encrypted, should be encrypted. One simple way to do this is to enable hard drive encryption on your PC or laptop. Most new operating systems make this as easy as changing a setting. This way if your laptop is stolen, the data cannot be retrieved without the password. While you’re at it, be sure to set up a longer pin or password on your phone. This typically encrypts the phone preventing someone from accessing the data on it.
Items like passwords should be stored in an encrypted container. There are online services that host these encrypted containers for you, some for free. Some services also offer sharing of passwords across accounts, allowing a team of employees to have access to certain passwords. For a local approach, there are free programs that can be used to store and encrypt a library of passwords. Make sure you select a program or service that is reputable and has a good track record of security.
Content Filtering & Antivirus
There are a lot of antivirus programs on the market today. Windows 10 also comes with a great antivirus called Windows Defender that’s free, built-in, and automatically enabled. No matter which antivirus you choose, it’s not going to protect you from all threats. Content filtering and a bit of user education will greatly improve your network security over just an anti-virus alone.
Content filtering can be done at the firewall level and at the client level. On the client side, I use an ad-blocking extension on all my browsers will malware filters added on. This prevents the browser from even visiting some domains that contain malware. Additionally, it often removes the sponsored click-bait that tempts the user to go to sites that contain pop-ups and other scripts that lead the user to install malware. On the firewall, content filters can be used to block inappropriate sites across the entire network. On production floor computers, firewall content filtering can be used to block nearly all internet access where it’s not needed.
Conclusion
We all have a responsibility to protect sensitive data that is stored on our networks. This Data Privacy Day, I encourage you to ask yourself the three questions I talked about above:
- What sensitive data is on my network?
- What are the access points to my network?
- How am I securing my data?
What are the additional items you came up with? Let me know in the comments below.
